Rule-based Access Control Can Be Changed by Users.
The Rule-Based Access Control also with the acronym RBAC or RB-RBAC. We use the term access control rules with a slight extension to denote the.
Rbac Vs Abac Access Control What S The Difference Dnsstuff
Organizations can and often do use different types of access control in different environments.

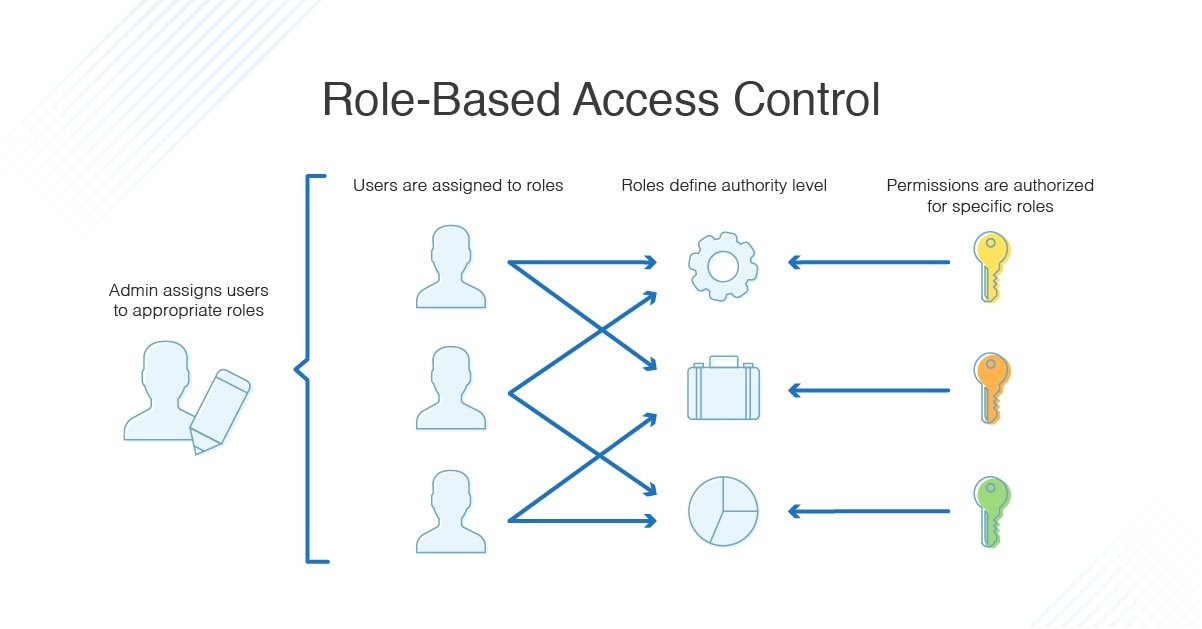
. Objects are the entities that receive access like networks and files. When the user is authenticated the Context information can be used to implement access permissions that depend on the users role. Users are sorted into groups or categories based on their job functions or departments and those.
All access permissions are controlled based on rules established by the custodian or system administrator. Rule-Based Access Control can be changed by users. This can make management of rights difficult.
Should be reasonably dynamic Example. As with MAC access control cannot be changed by users. The user update of a role is also an action you can do in case the access control does not provide expected access results in my blog How to analyze access control issues I will provide some more details on how to proceed in case of issues Sales Manager Bodo Mann.
When dealing with role-based access controls data is protected in exactly the way it sounds like it is. The local administrators group on the. Bellovin September 12 2005 13.
Implementation of Rules-Based Access Control systems is feasible so long as the number of triggering business events and the set of possible actions that follow those events are both. In this article. The access control rules presented here should not be confused with those implemented at the back end to control the access to the data by applications.
In Server Manager click Tools and then select AD FS Management. It applies boolean logic to grant or deny access to users based on the evaluation of atomic or set-valued attributes and the relationships between them. If user works in the Seattle office In Windows Server 2016 you can use an Access Control Policy to create a rule that will permit or deny users based on an incoming claim.
Access management for cloud resources is a critical function for any organization that is using the cloud. Attribute-based access control ABAC. On the Administrators tab you can control who can access Windows Admin Center as a gateway administrator.
In the name box enter a name for your policy a description and click Add. ABAC evaluates a set of rules and policies to manage access rights according to specific attributes such as environmental system object or user information. Examples of Rules Based Access Control include situations such as permitting access for an account or group to a network connection at certain hours of the day or days of the week.
Rule-Based Access Control can also be implemented on a file or system level restricting data access to business hours only for instance. Replacement worker Steven M. The system has total control over that object.
Access rights whether discretionary or mandatory need to change as the responsibilities of users change. The logic of if user is type a they can do x but not y is simple and easy to build. False With the Discretionary Access Control DAC model no object has an owner.
Domain-based Dynamic Access Control enables administrators to apply access-control permissions and restrictions based on well-defined rules that can include the sensitivity of the resources the job or role of the user and the configuration of the device that is used to access these resources. In this model users cant change anything. Bodo is the manager of the BFT Company Inc.
Software-based components to control access to resources. For example if someone is only allowed access to files during certain hours of the day Rule-Based Access Control would. Role-based access control is the norm in many companies For example a simple rule based on a user attribute might be.
Routers and such you can control rules on the network. In the console tree under AD FS click Access Control Policies. Once you have added a smartcard-based security group a user can only access the Windows Admin Center service if they are a member of any security group AND a smartcard group included in the users list.
Managing who or what in an ever-changing user base can access specific things or processes in an ever-changing systems environment. In the real world security policies are dynamic. Rule-based access control RBAC an access control model which specifies a set of common rules that apply to all usersresources and must be followed before access is granted.
To create a rule to permit users based on an incoming claim on Windows Server 2016. Azure role-based access control Azure RBAC helps you manage who has access to Azure resources what they can do with those resources and what areas they have access to. Right-click and select Add Access Control Policy.
Rule-Based Access Control will dynamically assign roles to users based on criteria defined by the custodian or system administrator. All access permissions are controlled solely by the system administrator. In addition to whatever type of access control you choose rule-based access control can change the permissions based on a specific set of rules created by the administrator.
Access management is basically gatekeeping. When a new user is authorized for a system the appropriate rights for that user must be established. Role-Based Access Control Permissions are granted to roles not users Map users to roles Any software problem can be solved by adding another layer of indirection Mapping can change.
In Windows Server 2012 R2. Role-based access control RBAC is one of the most common approaches with good reason. Similar to MAC Rule Based Access Control cannot be changed by users.
Subjects are the entities that do the accessing like users and applications. Rule-based control is often used in organizations when there is a need to organize say a network connection for.

Pin On Venkasure Total Security

What Do Those Lights On My Dashboard Mean Infographic Car Care Drivers Education Car Maintenance
Comments
Post a Comment